
Helping Grow Your Business
We provide you with a remote IT specialist who provides a wide range of IT services that contribute to the development of your business.

Control Your Network Switches
Networks are a group of devices connected together to share data and resources. These devices can include computers, printers, phones, and cameras, and use wires or wireless technologies to communicate with each other. The main purpose of networks is to facilitate communication and exchange of information between different devices, which contributes to improving efficiency and reducing costs.
Networks typically consist of several main components:
- Switches: Connect devices within a network and allow them to communicate with each other.
- Routers: Connect multiple networks together and help connect them to the Internet, analyze data and choose the best path to transmit it
- Wireless Access Points: Allow devices to connect to a wireless network without cables, making it easier to add new devices to the network.
Setup Your System Active Directory
Active Directory is a management system for Windows networks that allows the organization and management of network resources such as users, devices, and groups in a centralized manner. It was developed by Microsoft and is an essential part of the modern networking architecture. Active Directory is a vital tool for network management in large organizations, as it helps to:
Active Directory is a vital tool for network management in large organizations, as it helps to:
- Easy management: Reduces the need to manually update each device, saving time and resources.
- Improved security: Enables organizations to implement strict security policies and control access to sensitive information.
Active Directory is an essential component of modern network management, providing powerful tools to facilitate administrative processes and enhance security.


Manage and Secure Your Firewalls
Firewalls: A security system used to protect networks and computers from external threats. A firewall monitors and filters incoming and outgoing traffic based on pre-defined rules, preventing unwanted connections.
Firewall plays a pivotal role in cybersecurity through several key tasks:
- Prevent unauthorized access: Monitors incoming and outgoing traffic and prevents unauthorized access to your device or network by hackers or malware.
- Prevent cyber attacks: Helps protect against attacks such as DDoS (Distributed Denial of Service) attacks and phishing attacks.
In short, a firewall is an essential tool in securing networks and devices against growing cyber threats.
Check your system and update your devices to the latest version
System checks and updates are essential factors in maintaining the performance of devices and ensuring their security. These checks include updating operating systems and programs, which contribute to improving performance and fixing bugs and security vulnerabilities
The benefits you get from system checks and updates:
- Improved performance
- Security
- System compatibility
- User experience
Before performing any update, it is recommended to follow the following steps to ensure the success of the process:
- Back up your data
- Ensure that there is sufficient storage space
- Check your internet connection
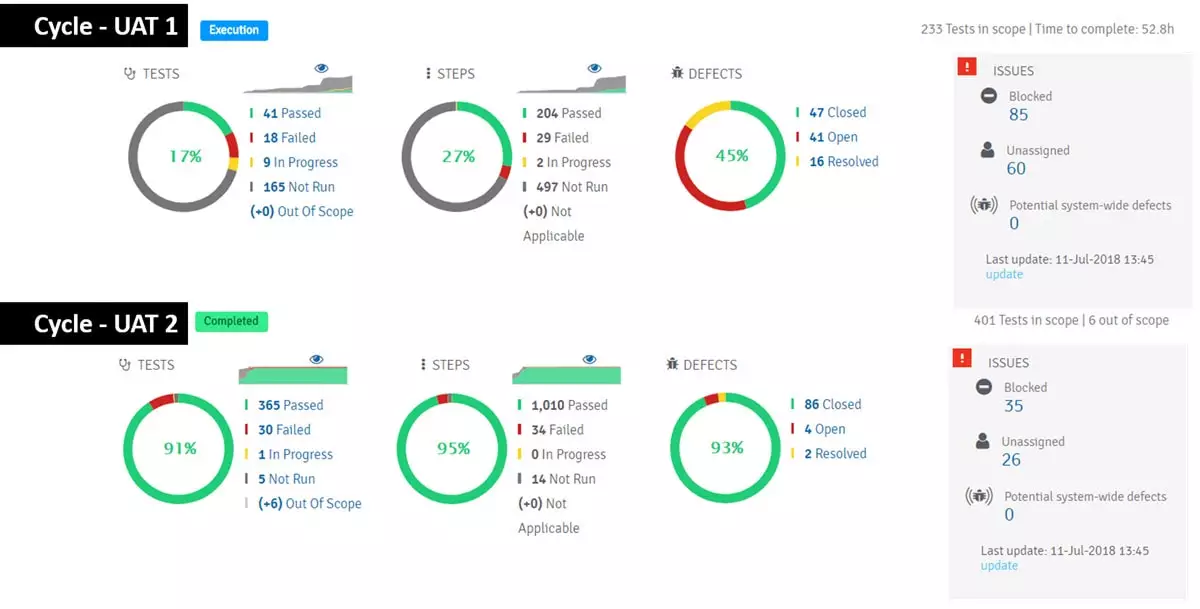
UAT System Receipt Test
To successfully conduct a user acceptance test, the following steps must be followed:
- Requirements Analysis: This includes reviewing key documents such as the project charter and business requirements document.
- Create a UAT Plan: This plan defines the strategy used to verify that the application meets business requirements, including entry and exit criteria and test scenarios.
- Define test scenarios: Test cases should cover most possible scenarios that end users might encounter.
- Test data preparation: It is preferable to use real data or data close to real data to ensure the reliability of the results.
- Running test cases and recording results: Test cases are executed and any errors or issues that arise during the process are documented.
- Verify business objectives are met: After completing the tests, testers must submit a report approving the product to be ready for launch.
